Below is an explanation from Tal Be'ery, Web researcher at Imperva, of why this is the case and what companies should be doing to ensure they do not fall victims to this crime:
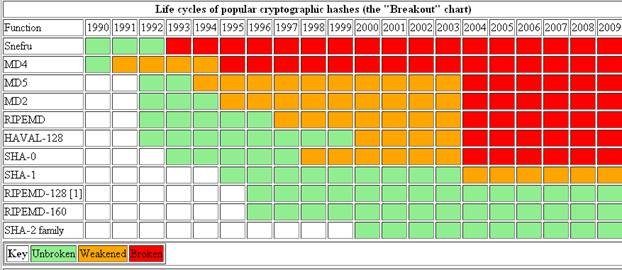
"The writing was on the wall, as this chart of the state of popular crypto hashes from 2009 (http://valerieaurora.org/...) shows:
The strength of the hash is expressed by its entropy or "randomness" and is measured in bits.The bigger the randomness, the harder it is for the attacker to guess the input that created the output of the hash function.
For example MD5 output is 128 bits long and SHA-1 is 160 bits long.
When the algorithm is found to be weakened it means that not all of the output bits are truly random, which means the attacker does not need to guess all of the output bits, just some of them.
For example, a researcher may find that instead of guessing all MD5 128 bits the attacker can guess only 120 and compute the remaining 8 bits. Guessing 120 bits is still a very hard task so the hash algorithm is not broken, just weakened. Although the algorithm is not broken, finding a weakness within it suggests that there are more undiscovered weaknesses that ultimately will allow attackers to break it. So the weakness should serve as a canary, or an early warning, that the clock is ticking for the specific hash algorithm and it should be replaced eventually.
When a crypto hash is weakened usually it marks the start of its downfall and SHA 1 has been weakened since 2004.
The consequence: in case the hashing is done for security (e.g. hash user passwords, verify data integrity, etc.):
- MD5 is dead and should never be used.
- SHA-1 is going in the same direction - so consider an upgrade of existing systems and definitely don't use it for new systems.
A smart choice would be to follow the U.S. National Institute of Standards and Technology (NIST) recommendation for federal agencies -
http://csrc.nist.gov/...
"Federal agencies should stop using SHA-1 for generating digital signatures, generating time stamps and for other applications that require collision resistance. "
So use a hash function from SHA-2 family - such as SHA256."