The Necurs botnet is notoriousfor its massive spam campaigns, believed to control over six million zombie bots. This botnet is most known for its ties to malware gangs that spread banking Trojans like Dridex and TrickBot, as well as ransomware such as Locky, Scarab, and Jaff.
But Necurs is not only about malware – its operators dabble in distributing spam for other fraud endeavors as well, which brings to light this recent romance scam campaign.
In 2017, X-Force has observed Necurs to send mass amounts of “pump & dump” stock scams designed to make recipients believe a penny stock is about to rise in value. Once enough people buy the stock, and it actually rises in value, the scammers sell off their shares, at which point they make a profit. The penny stock then drops back to its real market value and those who bought it can easily be left with nothing but losses. In early 2018, the botnet was part of large cryptocurrency scams, and this latest bout of dating spam is yet another major campaign linking Necurs with shady online activity.
Massive Spam in Season
Preying on seasonal trends is probably the top characteristic of email spam. The first quarter of the year typically plagues email recipients with tax season spam and romance scams that start arriving in January, leading up to Valentine’s Day.
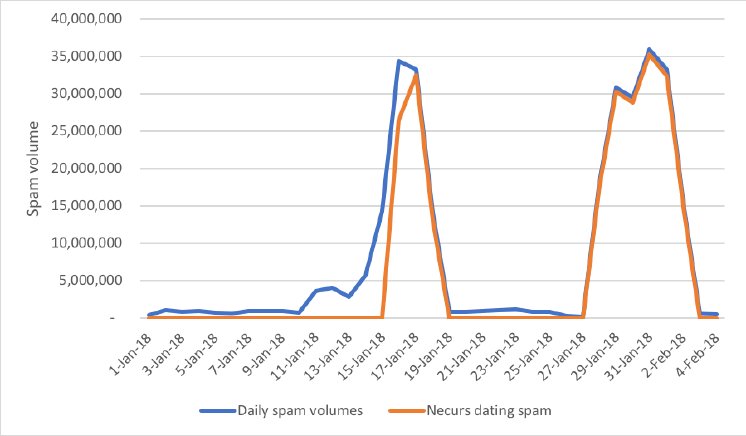
The current campaign from Necurs has reached over 230 million spam messages within a matter of two weeks, as the botnet speweddozens of millions of messages in two major bouts. The first surge started on January 16 through January 18 and the second surge started on January 27 and died down on February 3rd.
Well-Worded Spam
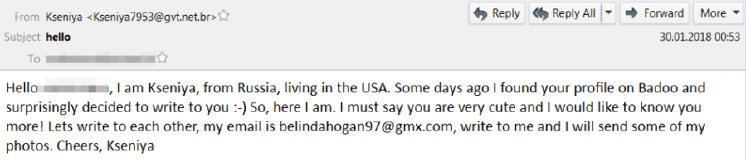
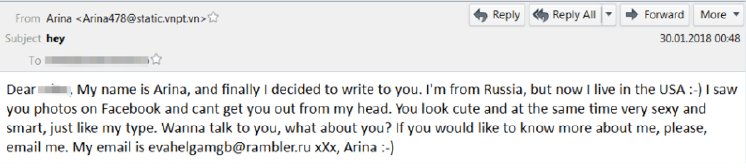
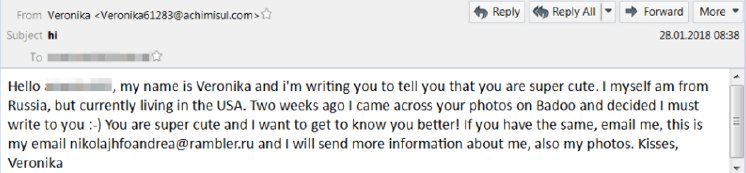
Looking at the messages being sent out in excess of 30 million emails a day, the current campaign delivers short email blurbs from supposed Russian women living in the US. While typical spam email is notorious for bad spelling and grammar, the samples are rather well-worded.
Each spam email comes from a disposable email address carrying the alleged writer’s name, but then asks the recipient to contact the writer back using another email address with another person’s name on it.
Many of the messages indicated that the recipient had a profile on Facebook, or on “Badoo” – a dating-focused social network, founded in 2006 by CEO Andrey Andreev, a Russian entrepreneur. Badoo is the third most popular dating app in Russia but is available internationally, which could explain the link between emails specifically from professedly Russian ladies to American men.
Romance scams and spam featuring messages from supposed interested women is an old ploy. Such emails usually feature nothing more than some basic text, and are not very likely to lure many people in. However, when it comes to spam, mass volume makes for a numbers game and the percentage of recipients that do reply. Those behind this campaign will likely lure their victims to share revealing photos and extort them, ask for money to come visit, or end up infecting them with malware.
Necurs’ Spamming Power
Overall in this vast campaign, X-Force recorded over 230 million dating spam emails from the Necurs botnet, bringing to light its current capacity to distribute very large amounts of junk email.
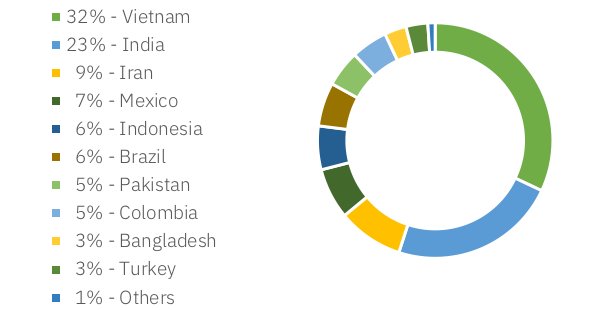
The spam was sent from roughly 950,000 different IP addresses. The top sender on the IP list was an address hosted via a Pakistani-based ISP. That IP address (103.255.5.117) had been reported as a spammer 655 times at the time of this writing and is currently rated as having a risk of 10 out of 10 according to the IBM X-Force Exchange.
The top senders were headed by Vietnam and India that, together, hosted originating IPs of 55% of the spam in this campaign.
It’s worth noting here that spammers constantly shuffle the resources they leverage in campaigns and the originating IPs logged in one campaign, are not likely to be used in the next one, in order to avoid blacklists and blocking.
After the recent takedown of the Andromeda botnet, and Avalanche before it, Necurs is probably the largest spam distributor serving cybercriminals at this time. X-Force research and ongoing monitoring of Necurs’ activity prove that its established status in the cybercrime world attracts both lower grade spammers and the elite gangs to its operators, in a quest to spread their malware and scams.
Say No to Spam
The operators of Necurs and other botnets task themselves with one goal: getting spam messages into people’s mailboxes without being filtered or blocked. These botnets often shuffle their methods to keep their “business” going, changing up the types of spam they spread and the ways to conceal it in varying file types and email ploys. As a result, it is possible that spam from Necurs would find its way into both consumer and employee mailboxes and the best way to thwart these emails is with employee awareness and education about the types of malicious emails that should never be opened or responded to.
Check out some of the advice from IBM Security on how to avoid taking spammer’s bait here: https://securityintelligence.com/mitigating-malware-modern-mobile-world/